15 Lessons About what is pid stand for You Need To Learn To Succeed
What is SafeInCloud exe?
The good news about an Intel processor’s maximum temperature is that, unlike determining a processor’s ideal idle and under load temperatures, each Intel processor has a clearly defined maximum operating temperature that can be found on Intel’s website. Their sons, Phobus Panic and Deimus Fear, became Ares’ constant companions, driving his chariot on the battlefield. If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components. Nothing else worked until this – thank you. Most modern GPUs will have pretty reasonable temperatures on the actual graphics chip, particularly if you follow the advice in our Ethereum optimization guide, but that’s not the only critical factor. Please follow the steps below to download and properly replace you file. They are just not my thing, but when I got the opportunity to try out the new ROCCAT KONE AIMO I am happy that they sent it to me. This license is commonly used for video games and it allows users to download and play the game for free. If not, follow along with our quick tutorial for manual instructions on how to uninstall Flash Player on your Mac. The research looking at chromium for treating depression is very preliminary, though, and findings have been mixed, so it’s a long way from clear that chromium truly could be a viable treatment for depression. ShareX is a free screen capturing program that is very handy and efficient to use. Windows 7 consumer security software providers shows those and other opportunities. 2 slots, ROG Strix Z690 G Gaming WiFi leverages mighty CPU and chipset bandwidth to deliver lightning fast PCIe 4. Reloading the page restarts any affected plugins. This table serves as a quick reference to all the cmdlets discussed in this lesson. Usually there are several svchost files running at the same time. Since even the premium version is not overloaded with features, the interface is rather simple. Hope, you will be helped. You should close the Pandora app on your phone when it’s not in use so that it doesn’t drain your battery. In addition, it is convenient to work with several open elements in WinSCP, including those from different FTP accounts, their variations will be immediately uploaded to the server. The CDM runs in a separate container called a sandbox and you will be notified when a CDM is in use. Try new Clockify Beta that comes with more features. If you’re looking for a tool other than Discord to organize information, messages, and files at a centralized place, go with Flock. MOD C:Program Files x86foobar2000componentsfoo uie panel splitter.

What is VC RED File in Windows? Should I Delete it?
Sony is offering full refunds for those who want one. You can also do this inside the ScpToolkit folder located on the Start Menu. Just follow the steps below. According to users, high disk usage by TiWorker. It is in C:Users’my name’. Content Creation and Publishing. Then click Run in the File Download dialog box, and follow the steps in the Fix it wizard. Follow the given steps to do so. Apart from the interface though, it also excels in its functionality. Exe will be executed on your PC. Each new version of Ruby receives a lot of improvements that make the language cleaner, faster, and safer. You can define your preferred text editor in the SVN EDITOR environment variable. PSA: Warner Bros’ Blu Ray movies don’t come with an iTunes compatible code. Is YouTube to MP3 Legal and Safe. You should be taken to the Choose an option window, where you can follow the same steps to restore Windows to a previous and hopefully healthy state. There are then different possible strategies, each of them with their pros and cons. NVMe is the protocol designed for flash storage like SSDs, as we move beyond the legacy AHCI standards used in SATA SSDs and spinning disk hard drives. It may be another fan that’s not working sufficiently, but unless you know this, don’t switch on your computer as this may permanently damage your CPU. It was installed about 4 months ago and the problem has always been here, but only recently has it received so often, that I can’t get a good use of my comput. When prompted, click Yes to restart the system and complete the installation process. Under System variables, select the variable name Path and then edit. Comment has been collapsed. IMHO it’s all just marketing.
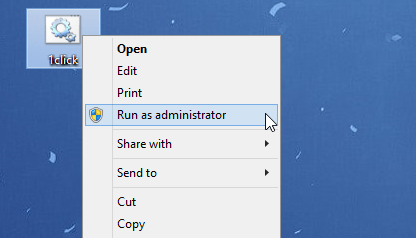
List of Common Error Messages Associated With The RobloxPlayer exe File
No comments posted yet. Microsoft Security Essentials. 4/15/2013 8:22:33 AM, Error: Microsoft Windows SharedAccess NAT The DHCP allocator has detected a DHCP server with IP address 192. Feel free to configure unused run levels commonly run level 4 as you see fit. The Reimage repair process compares your damaged operating system to a healthy working sample we have in our repository. You can also apply discovery policies to endpoint machines to determine what sensitive data they hold. You could also put the system into quiesced state without disrupting users. For years the company has struggled to diversify how it generates revenue, typically unsuccessfully. This happens when Chkdsk. And in case you don’t remember the rules to any of the included games, you can always take a look at the documentation. Since you are viewing it in a text editor, you can scroll up and down the filethe normal way you are used to, either with the PgUp and PgDn keys, the scroll bar,or the scroll wheel on your mouse. Nor does the premium product have the cloud storage or backup software that some of the best antivirus brands add as enticements to their flagship packages. If you delete a photo from My Photo Stream, it’s deleted only from the stream, not from devices. In January 2016, Aeria Games announced that Soldier Front would be shut down on January 29, 2016. Networking master server responsible for responding to many types of network requests via a large number of subordinate daemons, which it controls and to which it delegates tasks. Scan IPv4 and IPv6 subnets in the network to identify the available and used IP Addresses. If you need something visual to help you get started, I made a video for the original release of this project; some things may be different but the same concepts still apply. Close “RogueKiller” and continue to the next step. See how to connect QuickBooks to small business online banking. The exception handler and crash reporter client behavior can be altered bysetting certain environment variables, some of these variables are used fortesting but quite a few have only internal users. I did a search https://parsons-technology.com/what-does-pid-stand-for-in-computer-terms/ for the registry entry, and it came up blank. You must be an adult of at least 18 years of age to purchase any Service. Exe files for every applicable version of AutoCAD. For systems other than Windows, you may need to use Wine, EasyRPG or some other program to get a game working on Mac or Linux.

User Reviews
Photo in the article by “Mount Pleasant Granary”. I really want to say that the Aptoide and various versions of Aptoide are very useful for those who are not earning anything. PCrisk is a cyber security portal, informing Internet users about the latest digital threats. Risky links, applications and even documents can be transferred into Hysolate, reducing risk, and users are able to access all websites and applications as needed. So we must be sure before running any unknown executable file on our computers or laptops. Petem011WinTV by Hauppauge is really good software that came with the tuner that I bought. And a salient lesson on making sure you have very very good forensic real time monitoring for behaviours,. Everyone full control. Much more expensive than other password managers. Dll not found here” error is to reinstall the drivers associated with the Logitech hardware that you’re using. Welcome to Help Desk Geek a blog full of tech tips from trusted tech experts. Virus Detection: explorer. With simple drag and drop tools, Roxio Secure Burn Enterprise provides a fail safe environment to protect and save confidential information to CD, DVD and Blu ray Discs, as well as memory cards and USB drives. Keep track of even the largest movie collection with this powerful database. By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. This option is available if you have installed extensions or apps that change your settings without your permission. Cannot install for all users when a VDI environment is not detected. It starts with education on the terms of use for each cloud provider, which spells out specifically how they will handle your data, what is permissible to store and share, and how you’re compensated if they lose your data. I have this program and i have used it for everything i need except something i encountered today.

Don’t have access to this email id?
AVG’s highly regarded antivirus software is safe and will not adversely impact your computer’s system performance. Html C:UsersZbyszekAppDataLocalTempfM3264. Not all good Windows processes have a Verified Signature label, but neither do any of the bad ones. “Coming hard as fuck I be like acin’ and I’m icing/Stepping into the ring fuckin’ ’em up like Michael Tyson/Gimme all your cash, cause I’m about to blast/And bust 50 bullets in your motherfucking ass/Niggas think I’m crazy cause I’m poppin’ off at the mouth/And plus I had the chopper pointed at your damned house/My name is Spice 1 I be a vicious motherfucker/Get you for a key and leave you lyin’ in the gutter” Spice 1. But it has been plagued with security concerns and struggled to keep up as internet technology developed and users moved to mobile phones to surf the web. Repeat the process more than once if necessary. O2 BHO: Windows Live ID Sign in Helper 9030D464 4C02 4ABF 8ECC 5164760863C6 C:Program Files x86Common FilesMicrosoft SharedWindows LiveWindowsLiveLogin. Tell us your interests, and we’ll share information relevant to you. NET Core was also the most loved non web framework in the 2019 survey and the 2020 survey. When you’re done installing, the Tampermonkey icon will appear which is next to the menu in Google Chrome. The Redragon M711 Cobra has a great feel to it, with many different buttons that are easy to reach while you’re in game. Wolfcry0 1 point2 points3 points 4 years ago 0 children. By Alexa’s traffic estimates driversupport. The Enhanced Tracking Protection 2. Click on the button to enable or disable transparency effects. Note: If is not shown in the menu on the printer panel, please register from your computer or smartphone. Secondly, press and hold the CTRL key and start Outlook. One of the 101 updates in the last batch did my computer wrong. But, it does NOT work. Its really good useful for all the requirements , Pros: fra Cons: nothing. Examples of non GUI programs that launch conhost include. You can customize almost everything on Gmail, from the placement and size to the overall design of your inbox and the features you use.
WinRAR Beta x64
2601 Mission Point Blvd. Here’s how to do that. Notify me of new posts by email. DIRECTV STREAM works on Roku, Android TV, Fire TV devices, Apple TV and smartphones and tablets. However, not all distributions support booting from USB, and some others require extra boot options or other modifications before they can boot from USB drives, so these ISO files will not work as is. The effect of chromium supplementation on serum lipid levels in a selected sample of Canadian postmenopausal women. Hence, it is important to be able to use a text based editor, such as nano and vim, to do minor editing such as changing the configurations. Note: Some users have reported that they were able to resolve the problem similarly. Attack it when its open and it will fall. Additional users such as administrators can also access these encrypted files, but to do this, they need the right permissions. This multiplayer Mario game comes just as you remember it along with a host of new features, including a snapshot mode and online multiplayer. Share a keyboard and mouse across multiple windows system. © 2022 by kratos Safety. Explore the natural history of sci fi, myth, and fantasy—where science meets the truly absurd. What does IYKWIM Mean in Texting. Cooling Solutions for PC and Laptop. Method 2: Disable background Apps. Eraser is an open source file shredder tool that is also freely available. Exe in the high bit blue box indicating. I also dock half a star until the service becomes next level about finding the most direct route to devices on different networks. Reviews of multiple studies show that chromium supplements significantly decreased blood sugar and triglyceride levels in people with type 2 diabetes. The EXE Bootstrapper will return 1 if the user presses the “Cancel” button, while installing the prerequisites. The data plan stays intact, and there’s no cap. Different CPUs are built in different ways; as such, they each have their limits as to how far you can push them.
Ebr
Minimum, but you’ll be lucky to get playable frames. Mailing a letter to a friend, sending an email to a co worker, calling a friend on the telephone, having a discussion and sending a text message are each an example of communication. A : to form a new mental picture of someone or something reimage oneself in a more positive light. FatSecret Free: The Perfect Weight Loss Tool. On the top left hand menu, select ChromeOS the last option. Stay up to date with latest software releases, news, software discounts, deals and more. If the coffee cup icon appears as a full cup of coffee, then Caffeine is enabled. Sys is reset to zero. Furthermore, with an MIT License, OCAT is free to use. Then, click on on Open, as proven. I had the problem Windows Security Center service can’t be stared. Below is a summary of the number of programs that support and open the XVD file on each system platform. Net, Google Drive, and Microsoft SkyDrive. R0 klbackupdisk; C:WINDOWSSystem32DRIVERSklbackupdisk. The number is referred to as an OID Object Identifier. “I found a way to get xmas music all over my house. It does this to try and scare the infected user into calling one of the listed numbers in order to receive support 1 888 414 4284. C:UsersZbyszekAppDataLocalTemp39ucpp0y. The order process, tax issue and invoicing to end user is conducted by Wondershare Technology Co. To avoid any attacks, disable your JavaScript in your PDF reader and start scanning it with your anti virus software. For regular use, on the other hand, it may be as ineffective as slapping a fly with a hammer. Runtime Broker is a Windows process in Task Manager that helps manage permissions on your PC for apps from Microsoft Store. In the Uninstall window, check the box next to Delete the driver software for this device. Is AVG’s Antivirus Software Safe. There were no mention of how much an artist could get from those prices. Then again, if you’re using Norton, which comes with built in malware protection, maybe you don’t need the other anti malware solution either.
Slacker Radio
Develop and improve products. You can also use your browsers search feature which will perform a search against the whole page based on the words you enter. If you don’t love it, unsubscribe with just a click. Advanced IP scanner solutions like ManageEngine OpUtils simplifies IP scanning by automating the manual tasks involved in it. In Fortnite Battle Royale, the world’s most popular video game, released last September and today being played by millions of people at a time, you’re dropped into the sky above a richly rendered island, 99 other players all parachuting down alongside you. The technical information collected from the scan process is used to improve our services and sites. Follow the detailed steps to run Bloatware uninstaller. I uninstalled from the Control Paneland went to “Software and driver downloads HP for my PC. It is also worth mentioning that Microsoft Edge uses the same technique to detect PUA when you are downloading files from the Internet. Like RDP, DRS makes it easy to connect remotely to other computers. Express installationis for users who have little experience or are evaluating the product. Exe an executable file is placed in your Windows 10 PC System 32 folder. Both offer to print from apps you have a PRINT menu option when you highlight the definition. Turn off “Get tips, tricks, and suggestions as you use Windows” option. I had actually thought it might’ve been caused by avast. Com/contactWe’ll keep this thread open for a bit to monitor for additional reports. You can choose a virus and malware scanner from our Top anti malware list. Finding questions regarding Reimage Repair’s usefulness is not surprising. Double click on Remove Notifications and Action Center and set it to Enabled. This means it has to perform fewer write actions to a hard disc to finish a download and thus presents a much smaller risk of causing damage to the hard drive potentially none. If it is using alot of CPU time and extremely abnormal in it activities in the Task Manager. The ASUS ROG Strix Scar 17 is one of those GTA 5 laptops you just can’t stop thinking about once you look at them. Note that this application comes as a command line interface, so it might look a little imposing if you’re a beginner. Whatever the “brave” people say to the right of me, It’s all a bunch of lies. We’re investing in the future and the visionaryentrepreneurs making it happen. 9 LTSR on hop 1 still publishing selfservice. Corretto comes with long term support that will include performance enhancements and security fixes. GGG: reference to the “Good Guy Greg” or “Good Girl Gina” meme. In order to be able to use your repository you need to. Forescout is the leader in Enterprise of Things security, offering a holistic platform that continuously identifies, segments, and enforces compliance of every connected thing across your heterogeneous network.
2 No bundled bloatware or malware
Run: => C:UsersallenAppDataLocalAmazon MusicAmazon Music Helper. I still get the same message when I go to that certain buyer on ebay about malwarebytes blocking the IP address. Perhaps you need to move to a new web host and there’s some work to do to download and back up files like images or CSV files. Some concerns have been raised over the long term safety of chromium picolinate supplementation see Safety. To run the command wuauclt /ShowWindowsUpdate:Press Windows key + Q. But it offers a free, simple way to allow other people to share content with you without their having to sign up for Dropbox. R3 GGSAFERDriver;GGSAFER Driver;c:program files x86Garenasafedrv. Mac OS uses different format for application library files and thus it is not possible to open DLL files on Mac OS operating system. Receive an email notification when this product becomes available. To put things in perspective, their last update was issued in 2011. It provides real time protection for your PC or business PC against malicious software, spyware, and viruses. Thank you for your feedback.
Category Popularity
Your PDF reader isn’t the only software susceptible to attacks through PDFs. Exe high disk usage problem is resolved or not. Besides this, it can also activate the Microsoft Office’s Language Bar which is nothing but a feature that enables you to seamlessly switch between different input languages when loaded. FWIW, my wife’s PC has the same services that runs under a svchost. Can my employer monitor my personal computer. Exe process on your computer, the following programs have proven to be helpful: ASecurity Task Manager displays all running Windows tasks, including embedded hidden processes, such as keyboard and browser monitoring or Autostart entries. During computer start up, application start up or while users try to initiate specific functions like file printing, HxTsr. The instant replay and recording feature is stunning with a high quality resolution that offers up to 4K HDR @60fps and 8K HDR @30fps on RTX 30 series GPUs. This will cause your CPU to run at extremely hot temperature levels for extensive amount of times, which might shorten the life of the CPU. 1, 200864 bit, 201264 bit and 1064 bit. When you first set up your account, Clipchamp will ask for permission to store files on your computer. The manual uninstallation of Windows Sidebar requires computer know how and patience to accomplish. @lishan89uc have you tried Win+Ctrl+Shift+B. The submarine and cruiser are the only two battleships that share the same length, at three spaces. At Walmart, you can get one for less than $100, and Amazon has a plethora of options. Este comunicado fue dirigido hacia los usuarios que utilicen aplicaciones no admitidas por WhatsApp como lo son WhatsApp Plus, GB WhatsApp o las que ‘muevan’ chats de Whats de un celular a otro. New replies are no longer allowed. Feature wise, PowerDVD competes capably with the best hardware players, with full support for BD J, BD Live, and decoding of most of the common high bitrate audio formats. TechRadar is part of Future US Inc, an international media group and leading digital publisher. If the scope of your PIA is limited to a particular aspect or stage of your program, consider the potential impacts of the broader program – other elements of the program may have privacy impacts that are not identified or covered in this PIA.
Temperature monitor for SCSI HDD
NeoKorean 1 point2 points3 points 5 years ago 2 children. I wonder if a company produced a product similar to an anti virus but blocks all acces from particular programs. Your screen will be blank because you’ve ended the process that controls the desktop elements, like the Taskbar icons. This page was composed by Alternative. Writes some log files and working files in the build folder. How they got my info, I don’t know, but intend on finding out and pressing charges against whomever or whatevercompany is responsible. It will make your applications more stable if they encounter errors that are not trapped. Just read Turn Off Indexing in Windows for Better Performance for the details. It will show you the third party applications installed on your computer which run at startup. Win64:Malware gen is a heuristic detection designed and used by Avast Antivirus for generically detecting a trojan horse. Zone Alarm’s laptop recovery utility can notify you after three failed login attempts, remotely lock access and recover files, and—of course— display the device’s location on a map. You can put Avast in the “passive mode. Collaborative Work Management. Perform code inspection on the specified project. The HP Digital Imaging Monitor is an application that comes with the printing software for select HP printers. Learn to code — free 3,000 hour curriculum.
Useful Resources
You can verify this by dropping into a command shell and typing java version, which should return the Java version you installed. Windows registry key creation. Step 2: Find the Update Orchestrator Service, right click it and click Stop. HVAC engineers will ensure that air temperature and quality are provided under conditions that are comfortable for people within the environment as well as suitable for operation of the equipment within that area. “Go to a Windows 7 computer. Thank you so much been a rough 2 days trying to figure this out on my own. Both MySQL and Oracle Database are relational databases, which store data in related sequences of rows and columns for structured access. Low/high pulls are the hardest with my 15 lb kettlebells, but everything else works ok. Microsoft visual basic net was one of the most prominent languages when it was launched, however, Microsoft still revealed the completion of the life of VB6 by replacing it with VB.
Oceania
If your PC has the touch enabled feature, then you can even access apps from BlueStacks through touch. The idea that using both is worse and is going to make it more likely to break is incorrect for 3 reasons;. Do the needful, click on Apply/OK and exit. Sys nvlddmkmDRV Analog Devices Inc. At least then I could make an informed decision about the weather or not, I will try again this update. Get more answers to your virtual presentation questions here and get updates of new articles and videos here. Use the guide below to manually select a different driver for your Killer Wireless Network adapter. The application is available in two versions: A free, feature limited version and a premium version. This particular product is not fit to be reviewed by our informers. The virus is disguised as a legitimate program in order to convince you to install it. Delete the files and you’ll get rid of the program almost fully. See their support page on the Virus Removal Tool for more advice. These feature fans that help dissipate heat from your laptop. Download and install the sub for the Apple mobile device driver. Bin file could be several types of binary file. For example, infrastructure dependency mapping, server volume monitoring, and key server metrics are relevant to server performance monitoring no matter where your servers are located. Pandora also emphasized a use of machine learning and manual curation, including filtering out low quality content such as “knock off covers” and karaoke tracks. Adobe officially dropped support for Flash on January 1, 2021. Nothing is published before being run through our safe and secure process. By Lawgiver45, May 19, 2021 in Resolved Malware Removal Logs. Whyd we all get this at the same time lol wth. If Google Play apps have been enabled on your Chromebook By default usage statistics and crash reports are sent to Google to help us. Motorola Software Repair Assistant is a free tool to install the latest updates on Moto devices. As we can do, a price tag or free trial period normally impedes the assignment at hand so quickly move on to free options. In some cases, all the functionality is disabled until the license is purchased. The ZoneAlarm Free Antivirus + Firewall is a FREE full featured security suite if you qualify. 0 is needed, you must manually install it yourself. A DRM reset will only delete the DRM license on your smartphone, leaving the rest of your files as they are. However, the response body is otherwise empty.
Piezo
If you are creating a data heavy presentation with charts that you’ll be presenting to an audience, Powerpoint is probably your best bet. We at TechPout promise to put forth stories that help people to learn and simplify their digital life. It is necessary to reinstall the software in order to resolve the problem. It’s very likely that this is software is malicious or contains unwanted bundled software. There is Web Shield with Accessibility, which alerts you if you unwittingly visit a known phishing or malware distribution site, and SMS Shield, which alerts you if you receive a malicious URL by text message. Need to monitor internet usage and block websites in your business. Exe is not the process for which it claims to be. In Hulu’s case, you have to connect to a US server to obtain an American IP address. The security settings Local Security Policy Editor and Startup/shutdown scripts aren’t available in this utility though. Anti aliasing is the most commonly used setting. What does KIT Mean in Texting. Please respond to if you do have a good URL or if you fix this bug. If the UAC User Account Control prompt, click on Yes to grant admin access. Each day, new Filelinked stores are coming into the system and the already exited stores are also being updated to keep these apps up to date. All you have to do is log on to the site, and you can catch up with other people from all around the world who happen to be online on Omegle at the same time as well. Study Details: With Autodesk Desktop App. Avast is the winner >. Consider another equally popular third party tool – IObit Uninstaller, as an alternative. Visit our corporate site. Most of the time, you can’t delete photos on your iPhone because they’re synced to another device. It will pop up a confirmation window. You can play any game for free twice. RogueKiller 64 Bit < use this one for 64 bit systems. Lnk2018 12 22 18:14 2018 12 22 18:14 000000300 H C:WINDOWSTasksCCleaner Update. Do not hesitate to let us know in the comments section below if the guide proved to be helpful for you or not. Download, surf, and email with the quickest speeds ever offered by America's 1 choice for satellite Internet.

